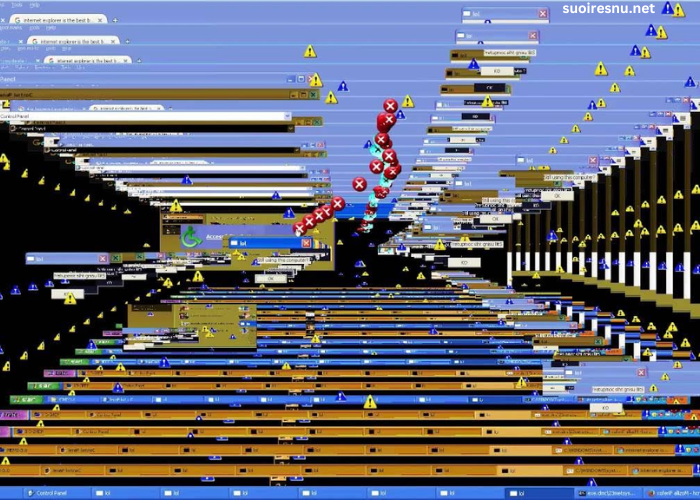
In the world of cybersecurity, malicious software, or malware, is a constant threat to users worldwide. One such piece of malware, Memz, stands out due to its unique blend of humor and danger. Memz is a Trojan horse designed to infect Microsoft Windows systems, and while it has a reputation for its pranks, it still poses a significant risk to your device and data.
Memz’s design is based on humor and shock value, targeting Windows systems by launching a series of increasingly bizarre and destructive actions. Initially, it might seem like a harmless joke, but as the infection progresses, its true harmful nature becomes apparent. The malware’s effects can range from computer crashes to data corruption, leaving users frustrated and vulnerable to further attacks.
In this blog post, we’ll explore the Memz Trojan, its characteristics, how it spreads, and how you can protect yourself from it. While Memz is known for its humorous approach, it’s important to understand the seriousness of Trojan horses and the potential consequences they carry.
Key Points After Introduction:
- Memz is a Trojan horse that affects Microsoft Windows systems.
- The malware begins with humorous pranks but escalates to destructive actions.
- Protecting your device requires awareness and proactive security measures.
What Is Memz and How Does It Work?
Memz is a type of Trojan horse—a malicious program that disguises itself as a harmless file or software to trick users into downloading or executing it. The term “Trojan” refers to the mythical Trojan Horse, where a deceptive gift was used to infiltrate the enemy’s defenses. Similarly, Memz lures users with seemingly harmless effects, but it harbors malicious capabilities.
Upon execution, Memz begins with seemingly innocent actions, such as displaying a few humorous messages or altering the appearance of the system. However, as the Trojan spreads deeper into the system, its pranks take a darker turn. The malware can delete files, corrupt data, or even damage the operating system itself.
Memz is known for its ability to persistently reappear even after an initial infection is removed. It can be especially dangerous because it often goes unnoticed in the early stages. Its methods of delivery typically involve tricking users into downloading it from untrusted sources, such as suspicious email attachments, fake websites, or even infected software cracks.
| Stage of Infection | Effects on the System | Impact Level |
| Initial Infection | Displays harmless pranks (like changing wallpapers). | Low to moderate |
| Progression of Infection | Corrupts files, deletes critical system files. | High |
| Final Stage | Damages the operating system, making it unbootable. | Critical |
Reminder: Memz may start with harmless pranks but quickly escalate to severe damage, so immediate action is essential.
How Does Memz Spread to Windows Devices?
Memz spreads in much the same way as other Trojans. Its most common method of distribution is through downloadable files from untrusted sources, including email attachments, torrents, or software cracks. These methods rely on the user’s willingness to download and run suspicious files.
Once the user executes the infected file, Memz is activated. Its code then works silently in the background, carrying out its pranks and attacks while the user may remain unaware. The Trojan can also exploit vulnerabilities in the Windows operating system or other software to spread and infect more files and programs.
In addition to spreading through infected files, Memz can also be distributed through malicious links. These links might be disguised as legitimate downloads or messages, but once clicked, they will initiate the Trojan’s execution on the system.
| Method of Spread | Description | Risk Level |
| Email Attachments | Infected attachments trick users into running them. | High |
| Software Cracks or Torrents | Users unknowingly download Memz with cracked software. | Moderate to High |
| Malicious Links | Links that lead to infected websites or downloads. | High |
Note: Be cautious about downloading files from untrusted sources, as this is the primary way Memz spreads to your system.
What Are the Symptoms of a Memz Infection?
The symptoms of a Memz infection are initially subtle and may go unnoticed. The Trojan begins with harmless pranks such as changing desktop backgrounds, displaying fake error messages, or creating random pop-ups. These are designed to entertain, but they are the first signs of the Trojan at work.
As the infection progresses, the system’s performance may degrade. You may notice that the computer begins to lag or crash more frequently. Files may become corrupted, and important documents or data could be deleted or damaged. In extreme cases, Memz can cause the operating system to become unbootable, rendering the device useless without a complete system reinstall.
Here are some common signs of a Memz infection:
- Random pop-ups or error messages.
- Unexplained changes to system settings or appearance.
- Slow performance or system crashes.
- Missing or corrupted files.
- Operating system failure or boot problems.
| Symptom | Description | Severity Level |
| Pop-ups & Error Messages | Unwanted messages or random pop-ups appear. | Low to Moderate |
| System Performance Issues | Slowdowns or crashes occur more frequently. | Moderate |
| File Corruption & Deletion | Important files may be corrupted or deleted. | High |
| System Boot Failures | Operating system becomes unbootable. | Critical |
Reminder: If you experience system crashes or strange behavior, it might be an indication of a Memz infection.
How Can You Protect Your System from Memz?
To protect your system from Memz and other Trojans, it is essential to adopt good security practices. Here are some proactive steps to prevent an infection:
- Use Trusted Sources for Downloads: Always download software, files, and applications from trusted websites. Avoid downloading software cracks or files from unverified sources.
- Install Antivirus Software: Use reputable antivirus software that can detect and block Trojans like Memz. Make sure your antivirus is up to date for the best protection.
- Enable Firewall Protection: A firewall can help block malicious traffic that might attempt to infect your system through malicious websites or email attachments.
- Avoid Clicking Suspicious Links: Be cautious about clicking links in emails or on websites that seem suspicious or unfamiliar.
- Regularly Backup Your Data: Backing up your data ensures that even if you become infected, you won’t lose valuable files.
| Protection Measure | Description | Effectiveness Level |
| Trusted Downloads | Only download from verified, trusted sources. | High |
| Antivirus Software | Use antivirus programs to detect and block Trojans. | High |
| Firewall Protection | A firewall helps prevent malicious access to your system. | Moderate to High |
| Backup Regularly | Backup your files to avoid data loss. | High |
Note: Regular software updates and practicing caution when downloading files are the best ways to prevent Memz infections.
Conclusion
Memz is an unusual Trojan horse in that it combines humor and harmful intentions. While it may start by playing harmless pranks on users, its potential to cause severe damage to your system is very real. Understanding how Memz works, how it spreads, and what signs to look out for can help you prevent it from infecting your system.
By taking steps such as avoiding suspicious downloads, using antivirus software, and maintaining regular backups, you can protect your Windows device from Memz and other types of malware. Always stay cautious and vigilant online, as the consequences of infection can be costly in terms of time, data loss, and device repair.
FAQ’s
- What is Memz and how does it work?
Memz is a Trojan horse that starts with harmless pranks but escalates to corrupting files and damaging the operating system. - How does Memz spread?
Memz spreads through email attachments, software cracks, and malicious links, often disguised as harmless files. - What are the symptoms of a Memz infection?
Common symptoms include random pop-ups, system crashes, file corruption, and operating system failures. - How can I protect my system from Memz?
You can protect your system by using trusted sources for downloads, installing antivirus software, and avoiding suspicious links. - What should I do if I get infected with Memz?
If you get infected, run a full system scan with antivirus software, and consider reinstalling your operating system if necessary to remove the Trojan completely.